In this modern era of advanced technology, safeguarding your valuable data becomes of utmost importance. From capturing cherished moments in photographs to preserving vital work files, taking proactive measures to ensure their security through reliable backups is a crucial step in protecting your digital presence. Allow me to present you with a detailed and all-encompassing manual on the art of crafting seamless backups, effectively fortifying the sanctuary of your digital existence.
Also read: How to Install and Use a Password Manager for Better Security
Step 1: Assess Your Data
Evaluating your data forms the cornerstone of initiating successful backup tactics. Devote sufficient time to classify your information into distinct clusters. Separate your individual records, treasured images, videos immortalizing priceless instances, your extensive music anthology, and all job-related documents. This methodical classification fulfills a critical objective—it provides an all-encompassing glimpse into the vast extent and multifaceted essence of the data that requires protection via backups. Comprehending the precise categories and volumes of data within reach not only streamlines the backup procedure but also guarantees a more meticulous and personalized strategy for safeguarding your digital existence.
Step 2: Choose Backup Methods
Local Backup:
Consider investing in a spacious external hard drive that offers ample storage capacity. Connect it to your computer and make use of its built-in backup software (such as Time Machine for Mac or File History for Windows) to establish regular backups.
If you have multiple devices in your household or office, it may be beneficial to explore Network Attached Storage (NAS). These systems provide centralized storage that can be accessed by all devices connected to the network, making automatic backups easier. NAS guarantees a convenient and efficient backup procedure, especially in environments where multiple users and devices require constant data protection.
Cloud Backup:
You might want to consider utilizing Cloud Storage Services from reputable providers like Google Drive, Dropbox, or OneDrive. It would be advisable to install their applications on your devices and customize settings to synchronize important folders or utilize dedicated backup functionalities. These well-known cloud services offer secure and easily accessible storage solutions for your data, guaranteeing seamless access and various backup options across different devices.
Furthermore, it would be beneficial to explore specialized Online Backup Services such as Backblaze or Carbonite. These services are explicitly designed for continuous and thorough backups, providing dedicated features to ensure the efficiency and reliability of your data protection. By leveraging these online backup solutions, you can diversify your backup strategy and enhance the security and redundancy of your digital assets. Each service offers unique features, allowing you to choose based on your specific backup needs and ultimately strengthening the overall resilience of your backup infrastructure.
Step 3: Establish Backup Schedules
To ensure the effectiveness of data protection, it is imperative to maintain a consistent backup schedule. Customize your schedule according to the importance of your data:
For Vital Data: Deploy daily backups or real-time syncing mechanisms. These frequent backups guarantee that any modifications or revisions to critical information are promptly secured, minimizing the possibility of losing data in critical scenarios.
For Less Significant Data: Contemplate a less frequent schedule, like weekly or monthly backups. Although these datasets may not necessitate real-time updates, regular backups at these intervals provide an additional layer of security by preserving different versions of the data in the event of unforeseen circumstances.
By aligning the backup frequency with the significance of your data, you establish a structured approach that prioritizes the protection of vital information while efficiently handling backups for less crucial data. This well-balanced strategy ensures the resilience of your data backup process without utilizing unnecessary resources for less essential information.
Step 4: Encrypt Your Backups
When it comes to dealing with delicate information, giving top priority to security is of utmost importance. Employing robust measures like encrypting your backups serves as a stalwart shield against any unwarranted access. A multitude of local and cloud-based backup services offer encryption functionalities meticulously crafted to fortify the defense of your valuable data.
To augment the security of your chosen backup services, be it local or cloud-based, consider enabling encryption settings. By encrypting your data, it is scrambled into an unreadable format, guaranteeing that even if unauthorized individuals manage to gain entry, they will be thwarted in their attempts to decipher or exploit the information.
For local backups, take a deeper dive into the encryption options found within the backup software or the settings of your operating system. Similarly, when utilizing cloud backup services like Google Drive, Dropbox, or specialized platforms such as Backblaze or Carbonite, navigate through the security or privacy settings to activate the encryption protocols.
By enabling encryption for your backups, you significantly mitigate the risks associated with data breaches or unauthorized access, thereby fortifying the overall security stance of the information stored.
Step 5: Test Your Backups
Frequently examining your backups is an indispensable measure in guaranteeing their dependability and effectiveness. By periodically attempting to reinstate files from your backups, you validate the integrity of the backup process and affirm that your data remains intact and accessible.
Commence test recoveries from diverse backups, encompassing both local and cloud-based repositories, to simulate real-world scenarios. Confirm that the restoration process executes seamlessly and that the acquired data corresponds to the original files. This practice assists in pinpointing any potential issues with the backups, such as tainted data or incomplete backups, enabling you to rectify them before encountering critical circumstances.
By regularly executing these tests, you proactively alleviate the risk of unpleasant surprises, ensuring that your backup systems are operating as intended. This proactive approach amplifies your confidence in the dependability of your backups, providing reassurance that your data can be successfully recovered when necessary.
Step 6: Diversify Backup Locations
It is absolutely critical to distribute your backups across multiple locations in order to mitigate the potential for catastrophic data loss. It is important to avoid the centralization of all backup copies in one location, whether it is a physical drive or a specific cloud service. Instead, it is recommended to establish redundancy by storing backup copies in various physical and remote locations.
One approach to consider is to maintain local backups on external hard drives or network-attached storage (NAS) systems, while also utilizing remote/cloud-based solutions such as Google Drive, Dropbox, or specialized backup services. By adopting this diversified approach, you ensure that even if one backup source is compromised due to hardware failure, theft, or technical problems, you will still be able to access your data through alternative backup locations.
By spreading your backups across different physical and remote destinations, you significantly decrease the likelihood of losing all of your data at once. This strategy of redundancy strengthens the resilience of your backup system and effectively safeguards your digital assets against the multitude of unforeseen circumstances or potential failures that could arise from relying solely on a single backup source.
Step 7: Automate Backup Processes
Take advantage of the automation capabilities provided by backup software or services to streamline your backup procedure. By utilizing automated backups, you significantly reduce the chances of overlooking scheduled backups and ensure consistent updates without the necessity for manual intervention.
Configure your backup software or cloud services to conduct scheduled backups at specified intervals, aligning them with your preferred backup frequency for crucial and less crucial data. Establish automated triggers that activate backups without requiring your active participation, ensuring that your data remains consistently protected without relying on manual execution.
Automated backups offer a hassle-free solution, eliminating the risk of human error or forgetfulness when initiating regular backups. They maintain the continuity of your data protection strategy by consistently and reliably backing up your information, providing you with peace of mind that your vital data is secure without the need for constant surveillance or manual backups.
Step 8: Implement Versioning
Certain backup systems incorporate the ability to include versions, enabling users to access previous iterations of files. This feature is extremely valuable, especially for documents or projects that undergo frequent changes. It empowers you to go back to previous versions whenever necessary, ensuring flexibility and security in managing evolving files.
The functionality of versioning keeps a record of changes made to files over time, allowing you to retrieve and restore specific versions from different points in the file’s history. In situations where errors are introduced or modifications need to be undone, this capability makes it easy to access previous versions, providing a safety net for critical documents or collaborative projects.
By using versioning in backup systems, you can navigate through different iterations of your files, promoting greater control and confidence in managing dynamic data. This feature acts as a safeguard against accidental changes or data corruption, allowing you to revert to a known good state whenever necessary.
Step 9: Monitor and Maintain Backups
Keeping a close eye on the status of your backups is of utmost importance for guaranteeing the efficiency and dependability of your data protection strategy. It is absolutely essential to validate that the scheduled backups are executing as intended and promptly address any issues that may come up.
Consistently reviewing your backup logs or monitoring tools is crucial to ensure scheduled backups occur as planned. If any discrepancies or failures arise, immediate action is imperative to troubleshoot and resolve the issues promptly. This proactive method aids in maintaining the integrity of your backup system, thereby ensuring the consistent safeguarding of your data.
Furthermore, it is vital to give priority to the physical well-being of the storage devices that house your backups. Adhere to recommended best practices, such as avoiding exposure to extreme temperatures, moisture, or physical harm. Handle storage devices with utmost care to prevent accidental drops or mishandling that may potentially compromise the integrity of your backups.
By systematically reviewing the status of your backups and diligently following proper maintenance practices for physical storage devices, you contribute to the overall solidity and dependability of your backup infrastructure. This proactive approach minimizes the likelihood of backup failures and ensures the uninterrupted protection of your invaluable data.
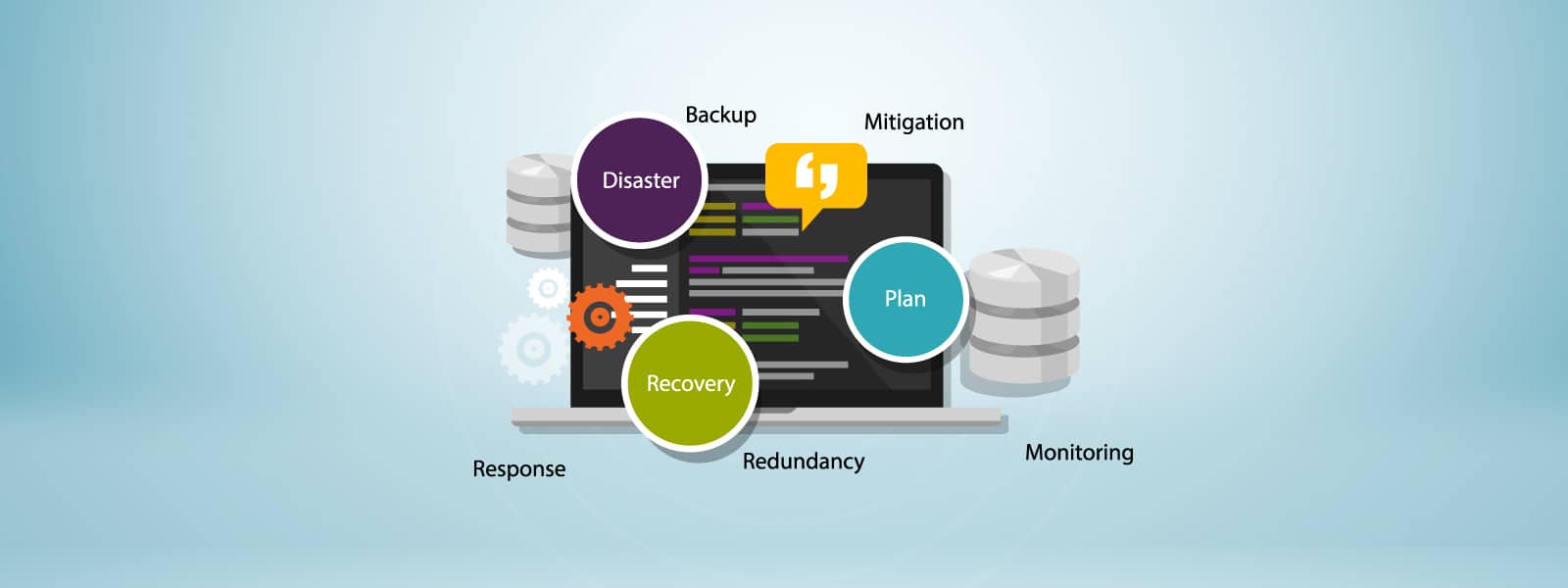
Step 10: Plan for Disaster Recovery
Prepare a thorough blueprint that outlines instructions to manage unexpected situations caused by hardware malfunctions, cyber breaches, or natural events, detailing steps to follow in case of data loss. This blueprint should incorporate protocols for data retrieval from backups and stipulate the individuals deemed responsible for overseeing the intricate recovery procedure.
Conclusion
Create a comprehensive blueprint outlining instructions to manage unforeseen circumstances like hardware malfunctions, cyber breaches, or natural disasters, guiding actions during data loss. This blueprint should incorporate protocols for data retrieval from backups and stipulate the individuals deemed responsible for overseeing the intricate recovery procedure.