In our increasingly digital world, it is vital to protect yourself from phishing scams. These scams are perpetrated by unethical individuals who devise deceptive schemes to trick unwary victims into revealing sensitive personal information such as passwords, credit card details, or social security numbers. To strengthen your defenses, consider the detailed advice below. These guidelines are designed to give you the knowledge and skills you need to navigate the online world safely. Being familiar with these safeguards will help you fend off phishing attempts and keep you safe online.
1. Be Aware and Educated
It is important to understand what phishing is and how it works. Phishing is a cyber threat in which bogus emails, websites, or messages pose as legitimate companies. These bogus messages often request sensitive information from their recipients. Recognizing the telltale signs of phishing, such as unexpected requests for personal information, can help you avoid becoming a victim.
It is important to be aware of common phishing strategies. Cybercriminals’ tactics for circumventing security measures are constantly evolving. Staying abreast of the latest scam strategies will help you spot suspicious communications. To successfully strengthen your digital defenses, regularly review the latest phishing techniques.
2. Verify the Source
Before taking any action, it is important to confirm that the sender’s email address is legitimate. Check the sender’s details carefully before connecting to the email or clicking on any attached links. Look for anomalies, such as minor changes to the sender name or domain, as scammers often use these methods to confuse victims.
Also, be wary of unsolicited emails, especially those requesting personal information. Legitimate companies do not often ask for sensitive information via email. If you have any doubts about the legitimacy of an email, contact the organization through proper channels before providing any personal information. Following these guidelines can reduce your chances of becoming a victim of bogus correspondence.
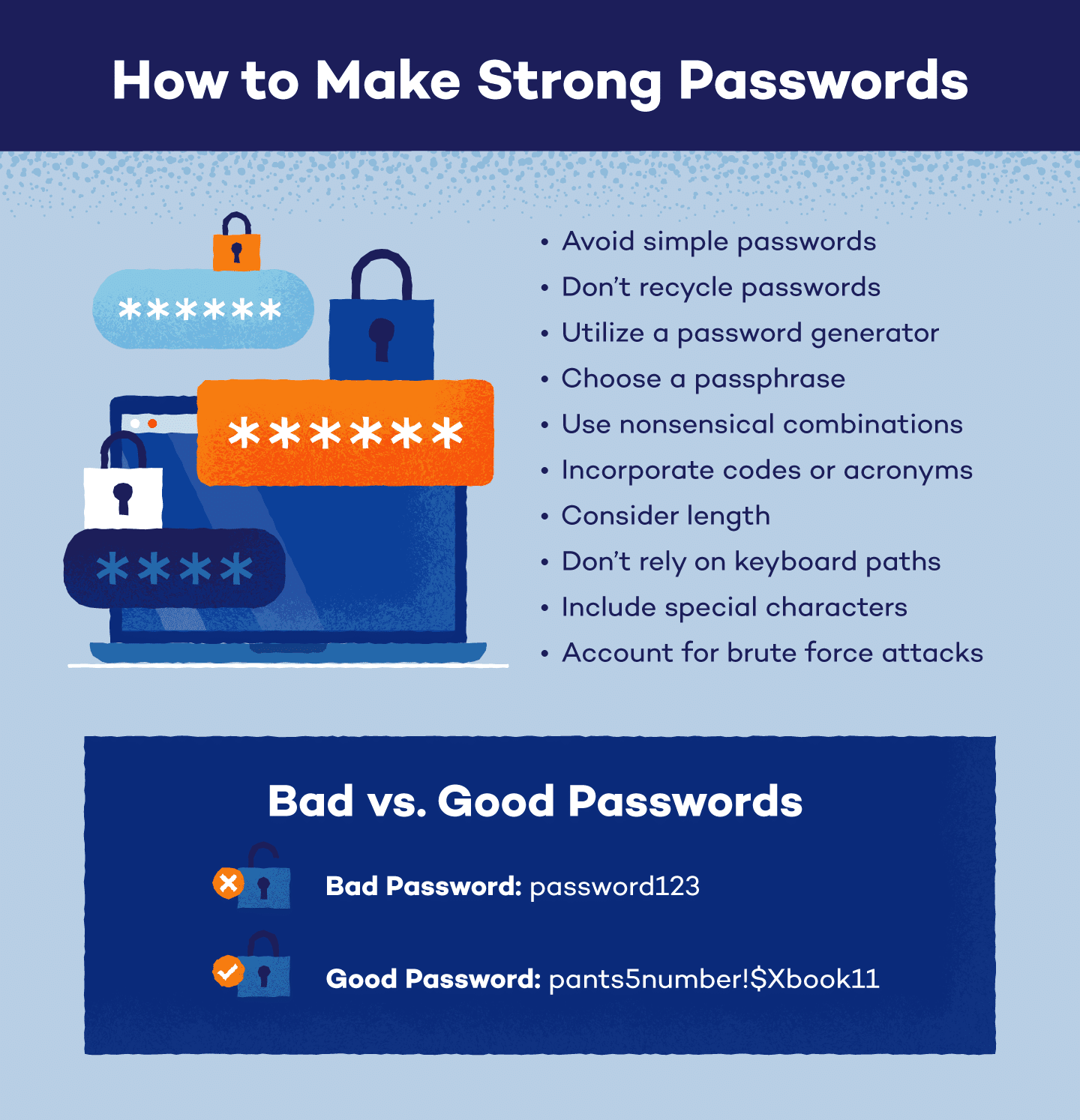
3. Use Strong and Unique Passwords
Creating strong passwords is an important line of defense against cyber threats. Create complex passwords by combining uppercase and lowercase letters, numbers and symbols. A strong password is one that is resistant to typical hacking tactics such as dictionary attacks.
Equally important is the practice of using unique passwords for each online account. This prevents a security compromise on one account from compromising the security of others. Consider using a password manager to manage a large number of passwords securely. These solutions store passwords and generate strong passwords, improving your online security. Following these guidelines can create a strong barrier against unwanted access to your accounts.
4. Enable Two-Factor Authentication (2FA)
Increasing the security of your account goes beyond passwords. Two-factor authentication (2FA) adds an extra layer of security. Wherever possible, enable 2FA for your online accounts. This feature requires an additional verification step in addition to your password. This usually involves receiving a unique code on your mobile device or via email that you need to enter along with your password.
Even if a malicious actor learns your password, 2FA dramatically reduces the risk of unauthorized access. It acts as a precaution against breaches and gives you added peace of mind that your accounts are secure. This method strengthens your online security posture and ensures that your personal information is kept safe.
5. Don’t Click on Suspicious Links
When it comes to links in emails or texts, vigilance is essential. Be careful and hover your mouse over links before you click on them. This will reveal the true destination of the URL. If the URL displayed does not match the official domain of the website you are visiting, do not click.
Be particularly cautious about links in unsolicited communications. Even if the message seems urgent, resist the urge to click unless you can confirm its validity. Cybercriminals often use urgency to motivate hasty activity. Following this strategy will reduce your chances of unknowingly visiting malicious websites or falling victim to phishing attacks.
6. Be Cautious with Attachments
Being careful with email attachments is an important aspect of internet security. Prudence dictates that you avoid opening attachments from unknown or unexpected sources. Cybercriminals regularly use attachments to deliver dangerous software, commonly known as malware, that can undermine the integrity of your computer.
Verify the sender’s identity and the email’s context before acting on any attachment. Even seemingly harmless attachments can contain hidden threats. If you are unsure about the validity of an attachment, do not open it. This precautionary approach protects you from accidentally activating malware that could damage your personal information or the operation of your system. Your cautious approach to attachments is important to your cyber protection strategy.
7. Check Website Security
It is important to assess the security of a website before sharing important information with it. A quick visual check is to check the browser address bar for two key clues. First, make sure that ‘https://’ appears at the beginning of the URL. This indicates an encrypted and secure connection, protecting your information as it travels.
Second, look for a padlock symbol next to the URL or in the browser’s status bar. This padlock symbol is a visual confirmation that the website uses security measures. Also, be careful to ensure that the website URL matches the organization’s official domain. Cybercriminals often use fake URLs to impersonate legitimate websites.
By following these practices, you can ensure that your personal and financial information is transmitted securely and that you interact with legitimate websites.
8. Be Skeptical of Requests for Personal Information
It is important to have a healthy skepticism about requests for personal information. Legitimate organizations rarely ask for critical information via email. If you do receive such a request, take a moment to consider its credibility. Cybercriminals often use phishing emails to trick people into revealing personal information.
If in doubt, contact the organization immediately using appropriate methods. Rather than relying on the information in the suspicious email, look up the official contact information on the organization’s official website or official documents. This approach can protect you from phishing attacks and protect your sensitive information.
9. Don’t Give in to Urgency or Fear Tactics
Cybercriminals often use urgency and panic as persuasion techniques to elicit hasty, unthinking responses. When confronted with messages that indicate an imminent threat or demand quick action, resist the urge to respond immediately. Instead, pause to consider the circumstances.
Consider the credibility of the communication by checking its claims against established facts. Such coercive measures are rarely used by legitimate organizations. Taking a minute to think will reduce the emotional pressure exerted by scammers and allow you to make an informed judgment based on logic rather than emotion. This level-headed approach greatly prevents succumbing to misleading haste or fear-based tricks.
10. Regularly Update Software
Updating critical software components in a timely manner is essential to maintaining the security of your digital environment. This includes your operating system, web browsers, and security applications. Updates fix vulnerabilities that criminals can exploit and also add new functionality.
Patches that fix security issues are regularly included in updates, making your system more resilient to cyber-attacks. These vulnerabilities may not be discovered until after the product is released, making updates an important safeguard against potential intrusions. Following a regular update schedule strengthens your digital defenses and reduces your vulnerability to attacks targeting outdated software.
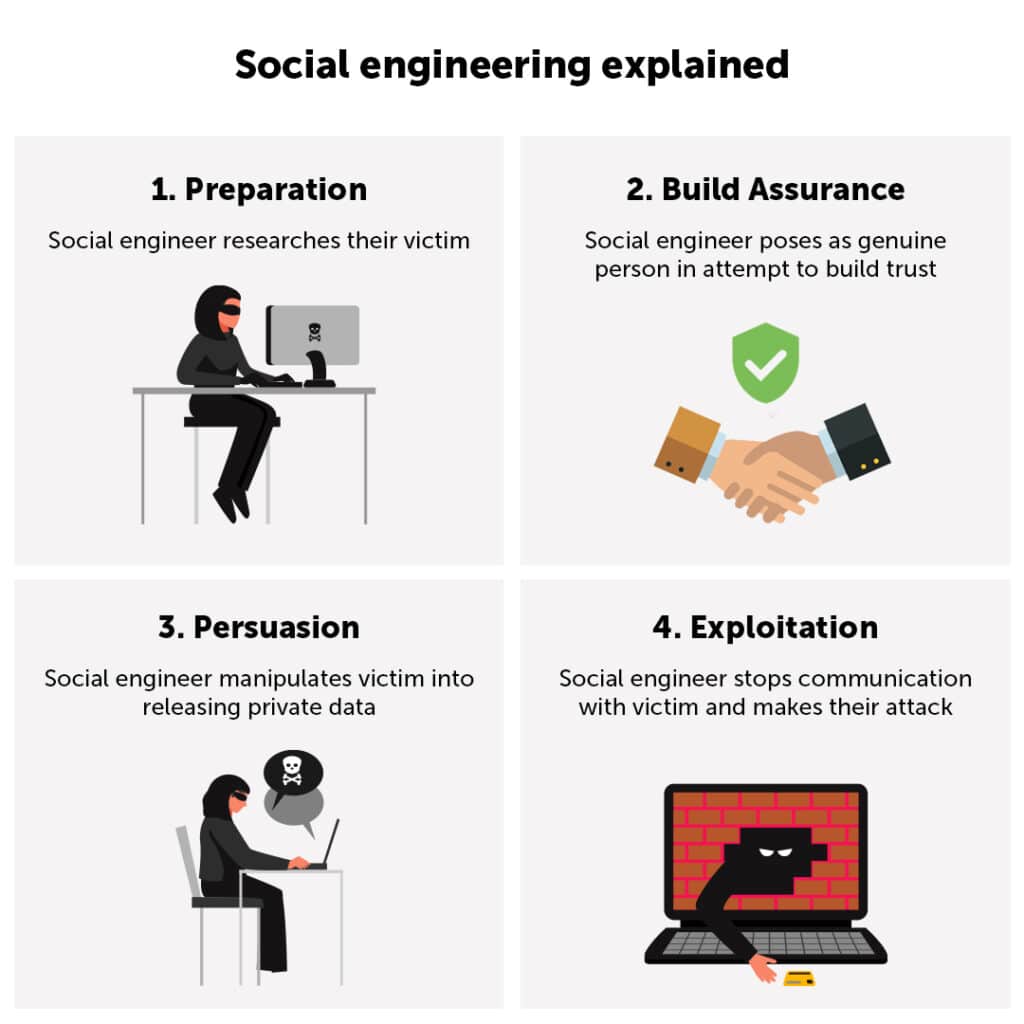
11. Be Wary of Social Engineering
Social engineering techniques are particularly damaging because they prey on your trust in people you know. Phishers often pretend to be someone you know, such as a friend or colleague, in an attempt to trick you. These fake messages may request sensitive information or activities that may seem innocent but could lead to a data breach.
Take a cautious approach. Before responding to such requests, independently confirm their validity using a variety of communication methods. To validate the authenticity of their request, contact them directly through a secure channel, such as a recognized phone number. By taking this approach, you create a barrier against falling prey to the deceptive strategies of social engineering.
12. Report Phishing Attempts
Taking a proactive approach to phishing means reporting any suspicious emails you receive. If you see a possible phishing email in your inbox, notify your email provider immediately. Many providers have measures in place to flag emails as phishing attempts, which can help other customers filter out similar communications.
You should also consider reporting the phishing attempt to the relevant authorities. Organizations such as the Anti-Phishing Working Group (APWG) are working to combat phishing and cybercrime. By reporting these events, you help the overall effort to detect and combat phishing attacks. By doing so, you protect your personal security and others from falling victim to the same deceptive techniques.
Also read: Select Fortify Your Online Accounts with Strong Passwords
Remember that staying aware and cautious online is essential to avoid phishing scams. Prioritize online security and apply these practices to all your devices and accounts.